Cyber Threat Intelligence is based on the collection of intelligence from multiple sources including Darknet and dark web, multiple forums and open source intelligence. This Cyber Threat Intelligence is used protect all your digital assets
Whether you think a breach might have already happened or if you want to make more informed security decisions, we can help you be proactive. Our managed Cyber Threat Intelligence service will provide you with rigorous analyses and monitoring of threats to your organisation and all your digital assets.
Unlike manual deep web analysis, Cyber Threat Monitoring periodically notifies you of any emerging threats.

Managed Risk &
Cyber Threat Intelligence Services
The services consist of an Artificial Intelligence driven Digital Risk Monitoring solution acting as a defensive component in scope of our Cyber Threat Intelligence Platform.
Powered by a powerful Cyber Threat Intelligence service It enables operators to evaluate, quantify, forecast, and mitigate the identified cyber threats and security challenges using comprehensive risk-scoring metrics to guide timely and strategic defensive actions. The platform and service allow to track security posture changes depending on the identified security events, Dark/Web/Surface Web, and other malicious activity. The platform and service identifies and eliminates potential blind spots and security gaps throughout your network infrastructure and exposed digital footprint. SecureIT and Resecurity offer managed threat hunting as part of the managed service offering, regular meetings to continuously improve customer security posture and make sure all digital assets are covered.
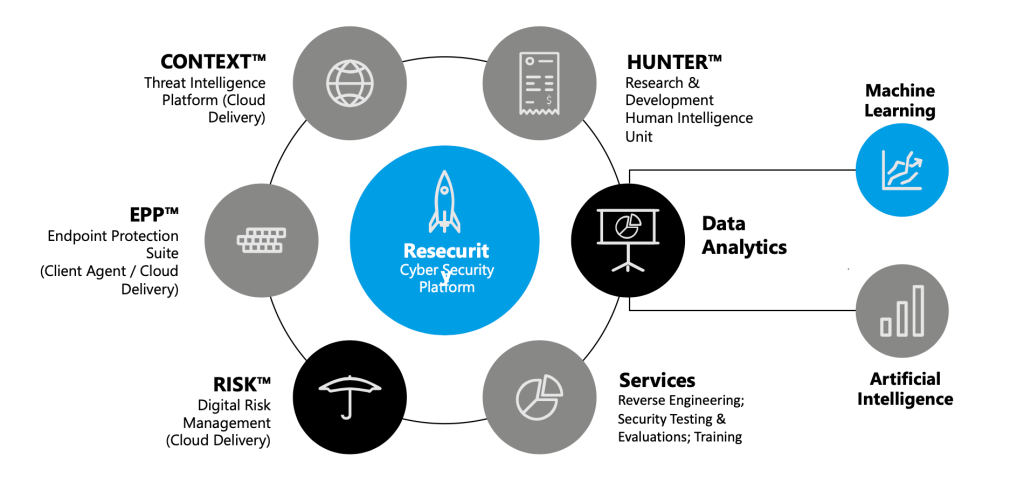
Key Differentiators & Benefits
Resecurity and SecureIT focus on actual threats, this is part of our DNA in building solutions and services based on data. Collected through global sensors supported by our human intelligence group. Providing tailored intelligence to each of our clients, unique to each of their missions.
Bottom line, we are data-driven intelligence and cybersecurity companies that focus on actual threats and manage those risks based on priority, urgency and value. Using the power of data, we solve not just one problem but for the entire enterprise and its ecosystem.Combined with world class experts, we provide tailored services beyond what is publicly.
We monitor all your digitals assets and risks which can include your supply chain and your vendor management as well as assisting in mergers and acquisitions.
RISK™ identifies external threats based on high-quality threat intelligence data aggregated from more than 20K public and proprietary sources.
Examples of benefits on how you can harness our managed security services and products:
Anti-Piracy
Holistic approach to piracy and counterfeit monitoring for various industry verticals. Prevent illicit distribution and use of your products, using actionable intelligence.
Brand Protection
Protect your brand from abuse, reputational risks, copyright infringement and intellectual property (IP) violations. Minimise loss of revenue, brand damage and loss of customer trust.
Dark Web Monitoring (DWM)
Lightning-fast search in the darkest corners of the internet. The biggest and constantly updating repository of underground communities and marketplaces (TOR, I2P, Freenet, IRC, IM-based).
Data Breach Intelligence (DBI)
Identify the exposure of sensitive data, such as intellectual property, confidential documents, customer and employee data. Prevent the risk of data breached in your infrastructure or clouds.
Digital Risk Monitoring (DRM)
Inventory your digital assets and control the risk across a variety of digital channels. Set up the settings of your digital footprint and get early warning notification.
Fraud & Risk Intelligence (FRI)
Discover the latest tools, tactics and procedures (TTPs) of fraudsters and cybercriminals targeting your enterprise. Use our SDK and the REST API in your apps and services to strengthen anti-fraud.
Investigations
Built-in case management system allows tracking of subjects of interest (SOI) in real-time and the centralisation of collected intelligence with proper tagging and context for further analysis.
Security Intelligence
Manage multiple internal and external threat intelligence feeds and enrich circulating threat telemetry in your SOC/SIEM/TIP for strategic decision making and proactive incident response.
Use Cases
Key examples of how our cybersecurity services products are used by Fortune 500 enterprises and governments globally.
Intelligence Agency
Situation: Source or Develop platform for National Intelligence Fusion Center
Impact: National Security
Resolution: CONTEXTTM used as centralised platform of Nation
Media
Situation: Intelligence monitoring during Winter Olympics 2018
Impact: Media and Public Safety
Resolution: CONTEXTTM used to monitor national and event threats related to Cyber Attacks
Financials
Situation: Combat against financial crimes
Impact: Wire Fraud
Resolution: CONTEXTTM modules like AML and Compromised Credentials to reduce fraud to 7%
Technology
Situation: Executive Protection for Board and Management
Impact: Brand Reputation
Resolution: RISKTM monitoring 250 key individuals and personal assets against active threats
eCommerce
Situation: Improve Supply Chain
Impact: Detect and be proactive against your supply chain
Resolution: RISKTM configuration of all ancillary and supply chain to monitor any weakness and defects
Government
Situation: Conduct investigation and engage threat actors on TTP
Impact: Cyber Warfare
Resolution: HUNTERSTM to conduct investigatory actions for operations globally
RISK™
RISK™ is Artificial Intelligence driven Digital Risk Monitoring solution acting as a defensive component in scope of Cyber Threat Intelligence Platform.
Powered by CONTEXT™ It enables operator to evaluate, quantify, forecast, and mitigate the identified cyber threats and security challenges using comprehensive risk-scoring metrics to guide timely and strategic defensive actions.
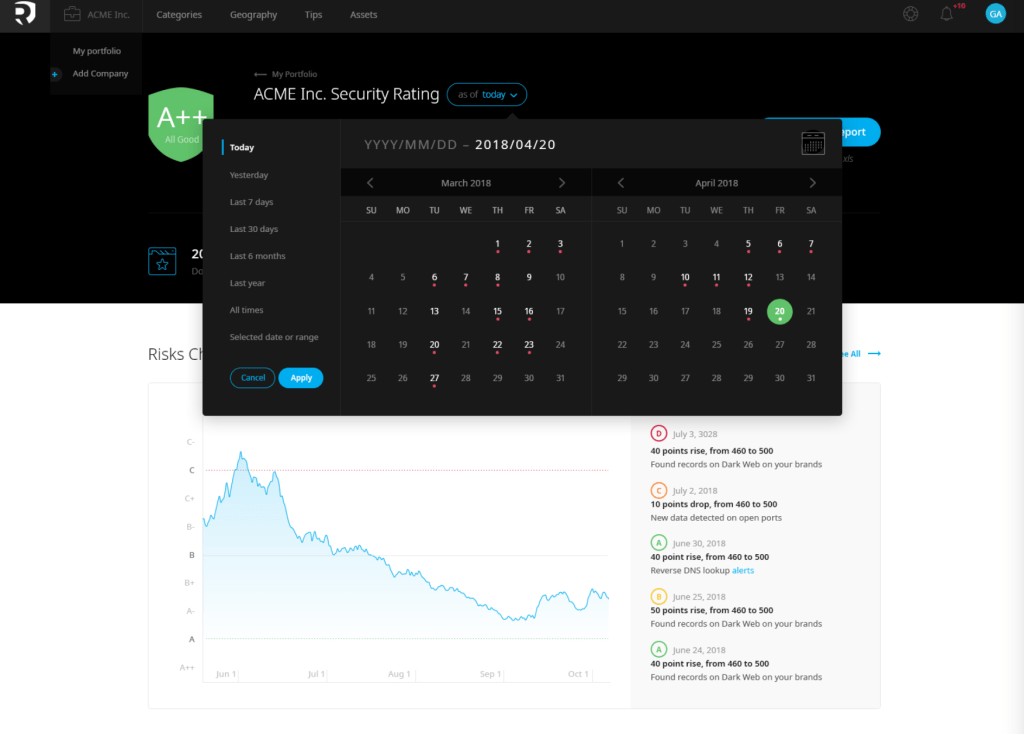

RISK™ allows to track security posture changes depending on the identified security events, Dark/Web/Surface Web, and other malicious activity.
RISK™ identifies and eliminates potential blind spots and security gaps throughout your network infrastructure and exposed digital footprint.
Key Advantages
Accurate
Artificial Intelligence driven engine will provide accurate insights that enterprises can act on and focus on.Scalable
Monitor any size digital presence, from a single domain to a globe-spanning network of applications, users, services and clouds.
Effective
Track evolving security risks in near real-time and respond proactively to mitigate vulnerabilities.
Comprehensive Monitoring
External
RISK™ identifies external threats based on high-quality threat intelligence data aggregated from more than 20K public and proprietary sources.
- Account Takeover (ATO)
- Botnet Infections
- Business E-mail Compromise (BEC)
- Cyberespionage
- Brand Reputation Abuse
- Dark Web Activity
- Domain Squatting
- Data Breaches
- Digital Certificates
- Exposed Network Services
Internal
RISK™ integrates industry standard security platforms to actualize the risk score of your enterprise footprint. Driven by your data, powered by Context™.
- Active Directory Account Compromises
- Backdoor Vulnerabilities
- Incorrect Network Segmentation
- Security Anomalies
- Lateral Movement
- Malicious Traffic
- Vulnerable Software
Baseline (Hardware, Software, Platform)
Configuration Errors
Unpatched Services
Cloud
RISK™ can monitor workloads in AWS and Azure around the clock, isolating and preventing attempted data breaches at the earliest stage.
- Monitor and alerts on abandoned EC2 instances
- Identify unsecured Exposed Databases
- Compromised Credentials
- Sensitive Data Identification
- Misconfigured services
- Malicious code
- Public S3 buckets with sensitive data
Key Features
RISK™ is delivered through a Software-as-a-Service (SaaS) model, which provides maximum flexibility and safety. It requires no installation or deployment on-premises. Your personnel identify the fundamentals of your digital footprint – such as enterprise domain names, IP addresses, and other digital assets – and Risk immediately begins to monitor those assets for threats. You can quickly see where assets may have been made vulnerable by historical security events as well as where emerging events pose new threats.
Within moments of onboarding, RISK™ has analyzed the security posture of your digital assets and characterized your exposure based on proprietary algorithm. Where the score indicates vulnerabilities, RISK™ provides actionable intelligence for direct remediation. As you resolve identified issues, your global cybersecurity score will improve.
RISK™ provides in-depth analysis and information about specific artifacts obtained through the dark web, botnets, passive DNS exploits, and other threat sources. You can examine each data point to understand the weaknesses and vulnerabilities of your digital assets. As new threats to your enterprise emerge from these sources, RISK™ provides timely updates and notifications.
To help combat alarm fatigue, RISK™ contextualizes risk information. It identifies threats of low, medium, and high risk to your infrastructure, network resources, and other company assets, making it easier to prioritize and act upon threats in ways that are both strategic and effective.
RISK™ can monitor your existing cloud platforms and services to ensure the integrity and security of your cloud-based infrastructure.
